As many readers already know, at VULNEX we have been working on our BinSecSweeper project whose development began in 2013 thanks to an award by US DARPA within its pilot program Cyber Fast Track (CFT) and we were the only Spanish startup to win a research award. In May 2014 I was invited to The Pentagon by DARPA to present my project, together with the other CFT participants. It was a unique and awesome experience!
Since then BinSecSweeper has changed in every way possible due to a strong engineering effort. With the rise of so many APT, I thought it would be interesting to analyze using Data Science techniques a recent APT that has gained a lot of media coverage: Equation APT Group.
For this analysis, I have got 419 Windows executables of this APT that we will proceed to examine with BinSecSweeper, let’s look at the results!
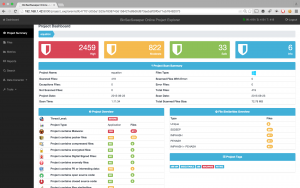
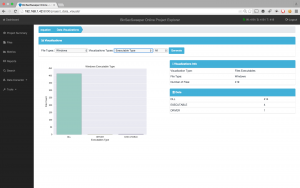
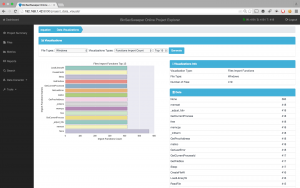
In Fig. 1 we have the project dashboard and we can see a summary of the analysis. BinSecSweeper has identified malware and high-risk vulnerabilities establishing a severe threat level alert (based on the US Homeland Security System). It draws our attention to different characteristics of the executables such as Packers, Personal Identifiable Information and binary similarities.
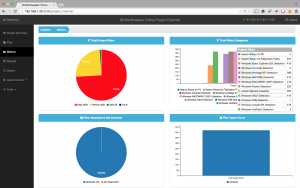
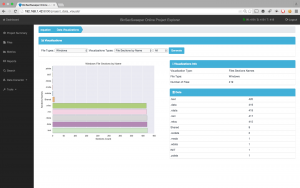
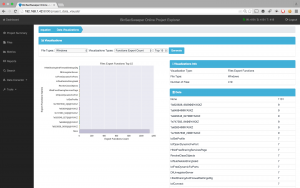
In metrics (Fig. 2) we see more details of the analysis, the metric that most interests us, at least to me, are the risks identified and the number of affected files. BinSecSweeper has identified interesting risks in this APT.
In BinSecSweeper we can deepen the analysis of one, several or all files, but for this high-level analysis our current objective is to obtain the big picture. So let’s look at the analytics data, a very powerful tool, see Fig. 3.
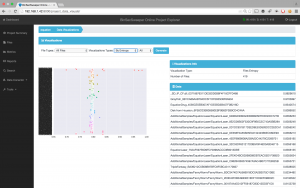
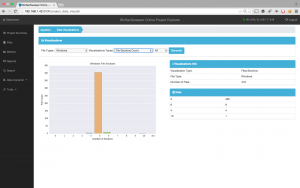
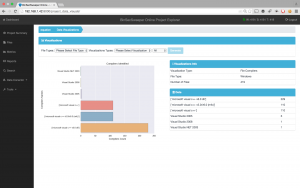
BinSecSweeper offers stunning graphics that help us to understand data very quickly and visually. In Fig. 4 we see a visualization of the entropy of the binaries. Most binaries are around 0.80 with some binaries in the 0.65 and 1.00 ranges.
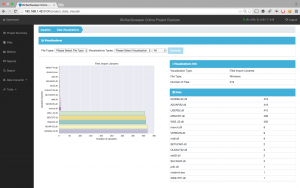
In Fig. 5 we can see the different types of binaries and should call our attention that most files are DLL and there is also one Driver, no doubt a file we should analyze in more detail.
In Fig. 6 we see a very interesting metric, section names of the executables. It helps us to identify suspicious sections and packers.
Fig. 7 is related to the previous metric, in this case we have the number of sections. There is a file with 10 sections.
The following metric (Fig. 8) we have the number of imported libraries by the executables.
Imported functions of the executables are interesting to understand functionality. In Fig. 9 we have this metric, specifically the Top 15 functions.
We can also see the exported functions, Fig. 10.
In Fig. 11 we see the identified compilers. It is interesting to understand the tools used by the APT authors.
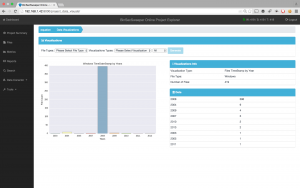
The last metric that we are going to see is the compilation timestamp of the executables organized by years. Clearly in 2008 the authors were very busy.
Very quickly and easily we have obtained a good understanding of this APT without entering into complex/costly analysis or reverse engineering, which would be our next step.
Today, with millions of malware circulating and the complexity of software, it is necessary to have in our arsenal powerful analysis tools such as BinSecSweeper, which uses advanced Data Science techniques to analyze the security and privacy of software.
Perhaps it would be interesting to analyze all antivirus with BinSecSweeper ;)
Hasta la vista Baby, I’ll be back soon with more analysis
For more information about BinSecSweeper you can contact us at BinSecSweeper@vulnex.com
Does your organization use Security Data Science? What would you like to analyze?
— Simon Roses Femerling / @simonroses