The other day helping out a client to develop secure software it came to my mind that this topic could be of interest to my readers. Obviously this topic is quite wide, but in this article I will focus in a patch for the GCC compiler, which improves the protection of stack protector (stack canary) mitigating buffer overflow vulnerabilities.
Stack Protector Strong is a patch developed at Google and applied to the Chromium project (browser Chromium and Chromium OS) that substantially improves this defense (StackGuard). By default on GGC we have the switches -fstack-protector and -fstack-protector-all that we can use to compile software: the first switch analyzes each function in the code and if it detects a possible vulnerability applies the defense when compiling the program (the programmer does not have to do anything, well just develop secure ;)), while the second switch applies the defense to ALL functions in the program without validating if they are vulnerable.
Both options have their respective problems: the first switch (-fstack-protector) is limited by the code it considers vulnerable while the second switch (-fstack-protector-all) is too aggressive affecting the performance of the application.
Because of these problems at Google they decided to develop a third switch, -fstack-protector-strong, covering more cases of vulnerable code without sacrificing performance. In figure 1 we can see a comparison between – fstack-protector and -fstack-protector-strong.
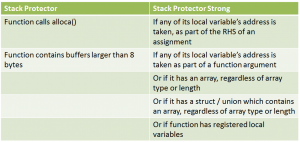
Fig. 1 – -fstack-protector vs. –fstack-protector-strong
Clearly a substantial improvement covering more types of possible vulnerabilities in code, but enough theory for today, let’s move on to a practical exercise where we will install the patch to the latest GCC 4.8.0 version, recently posted, on a Linux Debian 6.0.
The first step is to download GCC version that we want to patch. The patch was written for version 4.6, although I have tested with versions 4.7 and 4.8 and it works correctly. So we run the command wget with GCC URL and then unzip it (see figure 2).
To compile GCC we must have the following libraries installed and to install them we will use the command apt-get (see figure 3):
- Build-essential
- libgmp3-dev
- libmpfr-dev
- libmpc-dev
- zip
- autogen
Fig. 3 – Installing required packages to compile GCC
Now let’s download the -fstack-protector-strong patch from here. The patch is composed of 5 diff files.
We then proceed to patch GCC and we must follow the order that is showed in figure 5. Pay special attention to the order of the directories within the GCC.
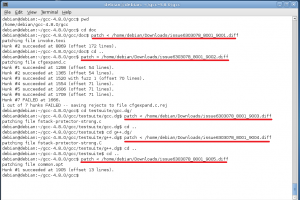
Fig. 5 – Applying patches to GCC
Once we have patched GCC we can compile it, for install it in the system we need to have root privileges (see figure 6). While the command is running you can read other articles on this blog since the process takes a while to complete 🙂
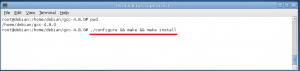
Fig.6- Compiling and installing GCC
Now we are ready to compile programs with the latest version of GCC and a better defense against buffer overflow vulnerabilities.
At figure 7 we compile a vulnerable program with the parameter -fstack-protector-strong.
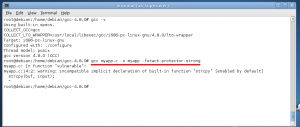
Fig. 7 – Testing –fstack-protector-strong
When disassembling (reversing) myapp we can see that this defense has been applied to several functions that -fstack-protector would have not applied (although I leave this exercise for another article).
This patch is not currently in GCC by default but let us hope that it will be in future versions as well as new and better defenses.
It is true that there are attack vectors to bypass this protection, but all defenses are welcome when building software and currently all modern compilers (GCC, Visual Studio and LLVM) include a variety of defenses that programmers should always use.
No doubt the use of these defenses in compilers does not remove the need for developing secure software using a secure development framework such as the MS SDL or OpenSAMM.
Which security parameters do you use when compiling software?
— Simon Roses Femerling