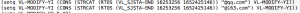Last June a malware that infected AutoCAD for Windows was identified and is responsible for the theft of thousands of documents. AutoCAD is a popular program for 2D and 3D drawings that is used to design all kinds of products, such as homes, cars, aerospace and in defense, so it is really interesting for industrial espionage. In this post we will study a malware known as Medre.
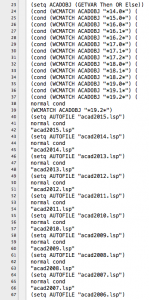
From a technical point of view is a simple malware, written in AutoLISP and scripts/payloads in VBS, but ingenious since it infects multiple AutoCAD versions in Windows (see Fig. 1) with the aim of stealing files and send them by mail to servers in China.
Fig. 1 – Supported versions of AutoCAD by Medre
In Fig. 2 we can see the Chinese servers where the stolen information is sent, Medre uses various email accounts on these servers. Despite using Chinese servers it is not entirely clear if the source of the attack comes from there.
Fig. 2 – Chinese servers
And in Fig. 3 we can see part of the code responsible for compressing the stolen files using WinRAR by setting the password “1”.
Fig. 3 – WinRAR code
If we think that AutoCAD is one of the most popular design programs that runs on multiple platforms such as Windows, MacOS and mobile (Android and iOS) it calls our attention the ingenious of this attack, simple and effective. Perhaps future malware versions will be multiplatform?
Without a doubt attacks to the industrial fabric either to SCADA systems or using malware like Medre to steal information are really interesting and dangerous to many organizations and Nation-States.
Which industrial espionage malware you found interesting?
— Simon Roses Femerling