Mirai is a DDoS botnet that has gained a lot of media attraction lately due to high impact attacks such as on journalist Brian Krebs and also for one of the biggest DDoS attacks on Internet against ISP Dyn, cutting off a major chunk of Internet, that took place last weekend (Friday 21 October 2016).
Besides the media coverage, Mirai is very interesting because we have both binary samples captured in the wild, but also because the source code was released recently – for sure we can expect many variants of Mirai code soon. Having both binary and source code allows us to study it in more detail.
It is quite amazing that we are in 2016 and still talking about worms, default/weak passwords and DDoS attacks: hello Morris Worm (1988) and Project Rivolta (2000) to mention a few.
Source Code Analysis
We have compiled Mirai source code using our Tintorera, a VULNEX static analysis tool that generates intelligence while building C/C++ source code. This gives us the big picture fast.
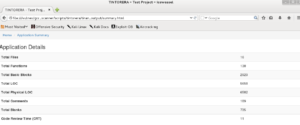
From Tintorera we get an application detail summary counting compiled files, lines of code, comments, blanks and additional metrics; Tintorera also calculates the time needed to review the code. Mirai is a small project and not too complicated to review. (Figure 1)
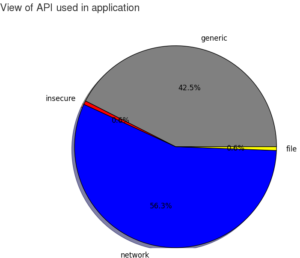
Mirai is using several functions from the Linux API, mostly related to network operations. (Figure 2)
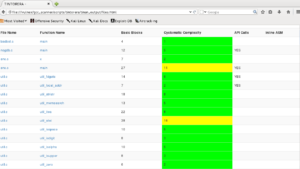
In the Tintorera intelligence report we have a list of files, functions names, basic blocks, cyclomatic complexity, API calls and inline assembly used by Mirai. By examining this list we can get an idea of the code. (Figure 3)
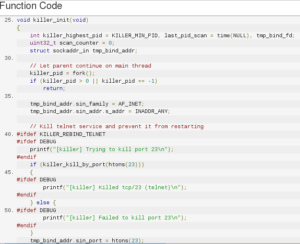
In file killer.c there is a function named killer_init that kills several services: telnet (port 23), ssh (port 22) and http (port 80) to prevent access to the compromised system by others. (Figure 4)
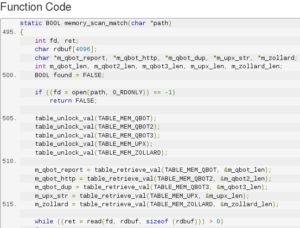
In same file, killer.c, another function named memory_scan_match search memory for other Linux malwares. (Figure 5)
In file scanner.c function named get_random_ip generates random IPs to attack while avoiding a white list addresses from General Electric, Hewlett-Packard, US Postal Service and US Department of Defense. (Figure 6)
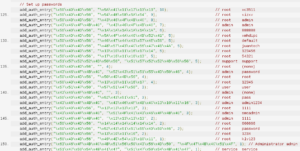
Mirai comes with a list of 62 default/weak passwords to perform brute force attacks on IoT devices. This list is setup in function scanner_init of file scanner.c. (Figure 7)
In main.c file we can find the main function that prevents compromised devices to reboot by killing watchdog and starts the scanner to attack other IoT devices. In Figure 8 we see a callgraph of file main.c
Mirai offers offensive capabilities to launch DDoS attacks using UDP, TCP or HTTP protocols.
Binary Analysis
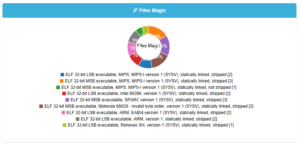
Now let’s move to binary analysis. So far we have been able to study 19 different samples obtained in the wild for the following architectures: x86, ARM, MIPS, SPARC, Motorola 68020 and Renesas SH (SuperH).
For the binary analysis we have used VULNEX BinSecSweeper platform that allows analyzing binaries among other things/files in depth combining SAST and Big Data.
In Figure 9 we see a chart showing all the files magic to give us an idea of the file types/ architectures. All samples are 32 bits.
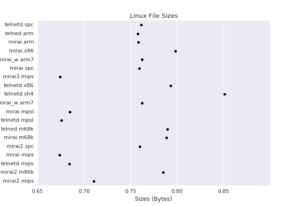
By using BinSecSweeper we obtained a lot of information for each sample, similarities between them and different vulnerabilities. Currently not many Antivirus identify all the samples, so beware what Antivirus you use! In Figure 10 we have a visualization of file sizes in bytes.
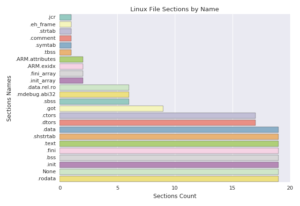
We analyzed all section names in the samples and Figure 11 is the result.
As mentioned before the samples are for different architectures so in this post we are not showing you the code analysis results.
We have updated BinSecSweeper analysis engine to identify Mirai malware samples. A full binary analysis report is available from VULNEX Cyber Intelligence Services to our customers, please visit our website or contact us.
Conclusions
Despite being a fairly simple code, Mirai has some interesting offensive and defensive capabilities and for sure it has made a name for itself. Now that the source code has been released, it is just a matter of time we start seeing variants of Mirai.
Mirai Botnet is a wakeup call to IoT vendors to secure their devices. Unfortunately millions of devices have been already deployed on Internet and there are insecure by default, so embrace yourself for more IoT attacks in the near future.
What do you think about IoT security?
— Simon Roses Femerling / Twitter @simonroses





Pingback: h6 – Arttu's Linux
Pingback: Tunkeutumistestaus H6 – https://christofferkavantsaari.wordpress.com